Doctors and nurses were running through wards, clutching pen and paper in their hands.
On Friday 12th May 2017, a major cyber attack took place to disrupt many organisations across the world. It affected more than 200,000 computers in 150 countries.
The cyber attack involved unknown hackers releasing a ransomware virus through to computer systems via email.
They affected an array of organisations such as FedEx, NHS and many others.
Hackers conducted the cyber attacks by sending a worm-infected email. It will contain a link or attachment that, once clicked, will release the virus and infect the computer. It will also infect the network and eventually the entire computer’s system.
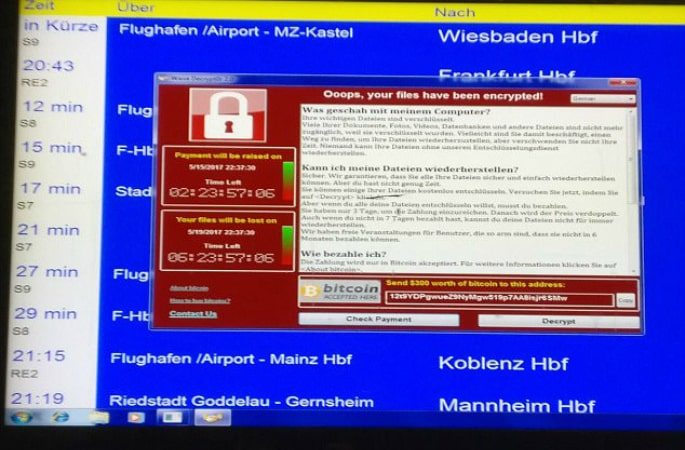
In this case, the hackers released a virus called the “WannaCry” Virus. It worked as ransomware, in that a red pop-window appeared on screens. It stated that the system’s files had become encrypted and they need to pay a ransom in Bitcoin currency.
Hackers claimed this ransom acted as the only way to access files or remove harmful programs.
Reverting NHS to the Past
In the UK, the cyber attack gathered national coverage as it breached the NHS computer systems. In fact, it targeted 48 NHS trusts in England and 13 NHS organisations in Scotland. During the attack, trusts that did not suffer the hacking turned off their systems too in order to prevent the attack.
This caused a huge impact for NHS staff. Patients recounted how doctors and nurses were running through wards, clutching pen and paper in their hands. Hospitals had reverted back to time.
They also faced delays as patients could not have tests or procedures on 12th May 2017, as they needed data files, contained on systems.
The NHS advised the public to only seek its services for urgent emergencies.
Including the UK, a total of 150 countries had companies that became infected by the ransomware virus. Companies such as FedEx in the US, Deutsche Bahn in Germany and Renault in France also suffered from the cyber attack.
While India and Pakistan have not suffered major attacks from the “WannaCry” Virus, their governments are keeping a check as experts released a “red alert” warning. They also will create webcasts to instruct computer users on how to protect themselves.
Luckily, a 22-year-old man named Marcus Hutchins was able to put a stop to the cyber attack. The IT expert found a “kill switch” for the virus in just a few hours. He claimed he found the switch by accident, yet it managed to stop the virus and save global companies.
On Saturday 13th May, his identity became revealed to the world as he created a blog. In the post, he explained how he accidentally found the virus’ “kill switch”. He supposedly shouted “Eureka!” when he realised he had stopped the attack.
Reports claim that he made the discovery while working at his parents’ home. The IT expert, who created a small hub for his triple-screen computer, now currently works with the National Cyber Security Centre.
Concerned about the risk of a mutated form of the “WannaCry” Virus, they are working to make sure a similar cyber attack doesn’t happen again.
Why did this happen so easily?
No doubt many around the world are asking this question. How did the hackers manage to pull off such a global attack? Well, there lies many reasons why it occurred.
First of all, the hackers may have tried to prove a point. Often, they will carry out these attacks to prove they had the capability to do so and show how weak security systems. Simply put, it gives them an ego boost.
While it shows the weak vulnerability points in company systems, the attack revealed how they still use old or outdated systems. In the case of the NHS, only a handful of trusts had installed new updates to their systems. While they didn’t suffer from the hack, those that didn’t have these new updates unfortunately did.
This also links to companies still using old operating systems, such as Windows XP. Combine this with the sheer number of computers using the same system, they are simply too outdated to prevent this type of attack from happening.
In addition, hackers have an expert knowledge of IT and generally are more intelligent as they can dedicate their lives to hacking. Compare this with a lack of IT staff and knowledge in companies.
Therefore, it seems this type of attack can very easily happen.
The Aftermath of “WannaCry” Virus
Since the shocking event, it has sparked a huge impact in the world of technology and politics.
Microsoft has described the cyber attack as a “wake-up call” and blamed the US government for creating such weak vulnerability points. They claim that the government stored data in vulnerable software, which could later become accessed by hackers.
In the UK, reports have now surfaced that its own government received warnings of an NHS hacking risk. Yet they did nothing. However, Prime Minister Theresa May denied the claims. She said:
“No. It was clear warnings were given to hospital trusts but this is not something that focused on attacking the NHS here on the UK.” She also revealed that £2 billion would be invested in cybersecurity in upcoming years.

Labour leader Jeremy Corbyn has also spoken about the hacking. He claimed that his government would pledge £37 billion into the NHS, improving its service. And, after recent events, improving its security with patients’ data.
And since Friday, many trusts still face the consequences. An anonymous GP has revealed how his surgery still has to rebook appointments and backlog information. He described the attack as “mindless”. He told BBC Asian Network:
“Cancer patients are getting their chemotherapy [appointments] delayed, simply because you haven’t got the information. What benefit can you get from that?”
Therefore, this global cyber attack has highlighted that there is a need for some type of drill. Similar to what they have with terrorist attacks, this hacking showed its potentially detrimental effects.
Currently, hackers come in three types. There are those who see it as a hobby and something to do in their pastime. In the news, many are familiar with the elite hackers, those who work for groups such as Anonymous, claiming to act for the greater good.
But then, there are those who hack with criminal intentions. With destructive motives, they act only to threaten and cause terror.
Will this continue to happen then? Yes, it will.
Cyber security acts only as good as its level of protection. This includes the use of passwords. If users use poorly selected passwords that are the same for many systems, this too can create weak points.
If companies have a lack of IT staff and knowledge and outdated computer systems, they will continue to appear as easy prey for hackers.